PKI Certificate Tutorials - Herong's Tutorial Examples - v1.12, by Herong Yang
PKI Certificate File Viewer and Decoder
This section describes two types of tools to see data fields encoded in PKI certificate files.
There are two types of tools you can use to see data fields encoded in PKI certificate files:
- Certificate Viewer - A graphical interface that decodes data fields from a given certificate and display them with field labels. Most Web browsers and operting systems provides you their built-in certificate viewers.
- Certificate Decoder - A command line tool or online tool that decodes data fields from a given certificate and display them with field labels. "openssl x509 -text" is not popular certificate decoder.
Here is a screenshot of the same certificate from the previous tutorial displayed by the default certificate viewer on a macOS system:
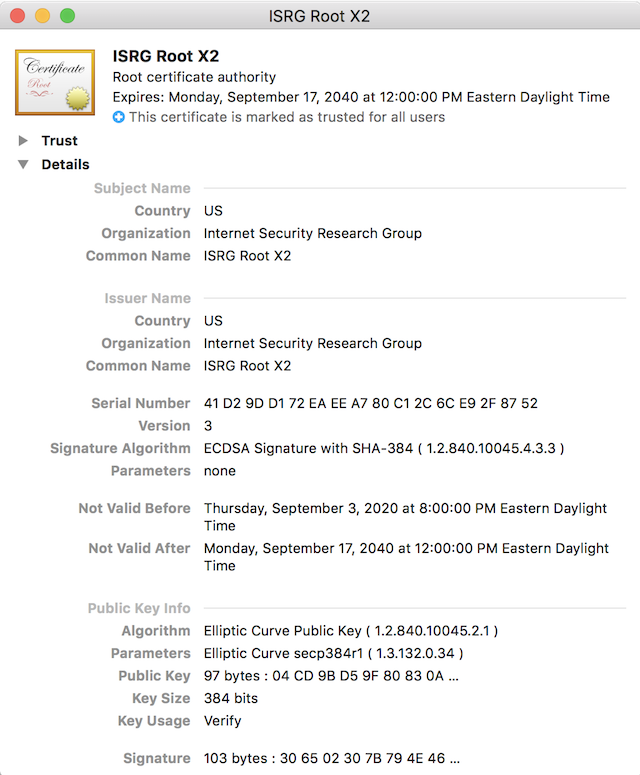
Here are the data fields of the same certificate printed out by the "openssl x509 -text" command:
herong$ openssl x509 -text -inform DER -in ISRG-Root-X2.der -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
41:d2:9d:d1:72:ea:ee:a7:80:c1:2c:6c:e9:2f:87:52
Signature Algorithm: ecdsa-with-SHA384
Issuer: C=US, O=Internet Security Research Group, CN=ISRG Root X2
Validity
Not Before: Sep 4 00:00:00 2020 GMT
Not After : Sep 17 16:00:00 2040 GMT
Subject: C=US, O=Internet Security Research Group, CN=ISRG Root X2
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
EC Public Key:
pub:
04:cd:9b:d5:9f:80:83:0a:ec:09:4a:f3:16:4a:3e:
5c:cf:77:ac:de:67:05:0d:1d:07:b6:dc:16:fb:5a:
8b:14:db:e2:71:60:c4:ba:45:95:11:89:8e:ea:06:
df:f7:2a:16:1c:a4:b9:c5:c5:32:e0:03:e0:1e:82:
18:38:8b:d7:45:d8:0a:6a:6e:e6:00:77:fb:02:51:
7d:22:d8:0a:6e:9a:5b:77:df:f0:fa:41:ec:39:dc:
75:ca:68:07:0c:1f:ea
ASN1 OID: secp384r1
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
7C:42:96:AE:DE:4B:48:3B:FA:92:F8:9E:8C:CF:6D:8B:A9:72:37:95
Signature Algorithm: ecdsa-with-SHA384
30:65:02:30:7b:79:4e:46:50:84:c2:44:87:46:1b:45:70:ff:
58:99:de:f4:fd:a4:d2:55:a6:20:2d:74:d6:34:bc:41:a3:50:
5f:01:27:56:b4:be:27:75:06:af:12:2e:75:98:8d:fc:02:31:
00:8b:f5:77:6c:d4:c8:65:aa:e0:0b:2c:ee:14:9d:27:37:a4:
f9:53:a5:51:e4:29:83:d7:f8:90:31:5b:42:9f:0a:f5:fe:ae:
00:68:e7:8c:49:0f:b6:6f:5b:5b:15:f2:e7
Note that field names are added the certificate tool, since they are not stored in the certificate file. And different certificate tool may give you slightly different names as shown below in the Java "keytool -printcert" output:
herong$ keytool -printcert -file ISRG-Root-X2.der Owner: CN=ISRG Root X2, O=Internet Security Research Group, C=US Issuer: CN=ISRG Root X2, O=Internet Security Research Group, C=US Serial number: 41d29dd172eaeea780c12c6ce92f8752 Valid from: Thu Sep 03 20:00:00 EDT 2020 until: Mon Sep 17 12:00:00 EDT 2040 Certificate fingerprints: SHA1: BD:B1:B9:3C:D5:97:8D:45:C6:26:14:55:F8:DB:95:C7:5A:D1:53:AF SHA256: 69:72:9B:8E:15:A8:6E:FC:17:7A:57:AF:B7:17:1D:FC:64:AD:... Signature algorithm name: SHA384withECDSA Subject Public Key Algorithm: 384-bit EC (secp384r1) key Version: 3 Extensions: #1: ObjectId: 2.5.29.19 Criticality=true BasicConstraints:[ CA:true PathLen: no limit ] #2: ObjectId: 2.5.29.15 Criticality=true KeyUsage [ Key_CertSign Crl_Sign ] #3: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 7C 42 96 AE DE 4B 48 3B FA 92 F8 9E 8C CF 6D 8B 0010: A9 72 37 95 ] ]
Table of Contents
Introduction of PKI (Public Key Infrastructure)
Introduction of PKI Certificate
What Is ASN.1 (Abstract Syntax Notation One)
What Is BER (Basic Encoding Rules)
ASN.1 Type Modifier - Type Tagging
What Is DER (Distinguished Encoding Rules)
PKI Certificate Structure in ASN.1 Notations
PKI Certificate in Base64 Format
►PKI Certificate File Viewer and Decoder
PKI Certificate File ASN.1 Parser
Certificate Wrapped in PKCS7 Formats
Certificate Wrapped in PKCS12 Formats
Certificate File Format Summary
OpenSSL - Cryptography Toolkit
"openssl ca" - CA (Certificate Authority) Tool
Java "keytool" Commands and KeyStore Files
PKCS12 Certificate Bundle File