Windows Security Tutorials - Herong's Tutorial Examples - v3.01, by Dr. Herong Yang
Building "ignorelist" for HijackThis
This section provides a tutorial example on how to build a list of system settings and file settings for HijackThis to ignore during system scan.
While reviewing the HijackThis scan report, if you see entries that are legitimate, you can put them in the "ignorelist". Those legitimate entries will not show up again in the next scan.
1. Double click "C:\local\HijackThis\HijackThis.exe". You will see HijackThis started with its main menu:
2. Click the "Do a system scan" button. You will see the scan report display in the HijackThis windows.
3. Check the checkbox for each entries that are legitimate. For example, I checked the following entries:
O2 - BHO: MSS+ Identifier - {0E8A89AD-95D7-40EB-8D9D-083EF7066A01}...
O2 - BHO: Java(tm) Plug-In SSV Helper - {761497BB-D6F0-462C-B6EB-D...
O4 - HKLM\..\Run: [LENOVO.TPKNRRES] C:\Program Files\Lenovo\Commun...
O4 - HKLM\..\Run: [Microsoft Forefront Client Security Antimalware...
O4 - HKCU\..\Run: [Skype] "C:\Program Files\Skype\Phone\Skype.exe"...
O4 - Global Startup: Bluetooth.lnk = ? ...
O4 - Global Startup: McAfee Security Scan Plus.lnk = C:\Program Fi...
O8 - Extra context menu item: Send image to &Bluetooth Device... -...
O8 - Extra context menu item: Send page to &Bluetooth Device... - ...
O9 - Extra button: @C:\Program Files\ThinkPad\Bluetooth Software\b...
O9 - Extra 'Tools' menuitem: @C:\Program Files\ThinkPad\Bluetooth ...
O23 - Service: Bluetooth Service (btwdins) - Broadcom Corporation....
O23 - Service: SMS Task Sequence Agent (smstsmgr) - Unknown owner ...
O23 - Service: Lenovo Hotkey Client Loader (TPHKLOAD) - Lenovo Gro...
O23 - Service: On Screen Display (TPHKSVC) - Lenovo Group Limited ...
...
4. Click the "Add checked to ignorelist" button.
5. Click the "Config..." button. You will see the configuration screen.
6. Click the "Ignorelist" button. You will see the list of entries that you want the HijackThis scan process to ignore them, because they are legitimate.
The picture below shows the list of system settings and file settings to be ignored during HijackThis system scan:
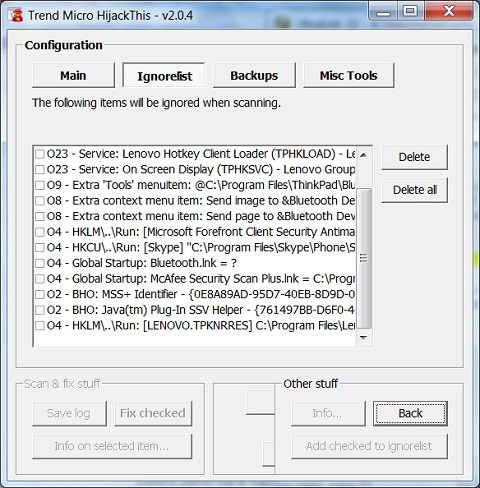
Table of Contents
About This Windows Security Book
Windows 8: System Security Review
Windows 8: System Security Protection
Windows 8 Defender for Real-Time Protection
Windows 7: System Security Review
Windows 7: System Security Protection
Windows 7 Forefront Client Security
Norton Power Eraser - Anti-Virus Scan Tool
McAfee Virus and Malware Protection Tools
Spybot - Spyware Blocker, Detection and Removal
Keeping IE (Internet Explorer) Secure
Malware (Adware, Spyware, Trojan, Worm, and Virus)
►HijackThis - Browser Hijacker Diagnosis Tool
Downloading and Installing HijackThis
Scan Report Generated by HijackThis
HijackThis Log File Entry Types
►Building "ignorelist" for HijackThis
Fixing Settings Reported by HijackThis
Generating Startup Program List by HijackThis
Listing Processes and DLL Files with HijackThis
Listing Installed Programs with HijackThis
HijackThis Configuration Settings
IE Add-on Program Listing and Removal
"Conduit Search" - Malware Detection and Removal
"Tube Dimmer", "Scorpion Saver" or "Adpeak" Malware
Malware Manual Removal Experience
Vundo (VirtuMonde/VirtuMundo) - vtsts.dll Removal
Trojan and Malware "Puper" Description and Removal
VSToolbar (VSAdd-in.dll) - Description and Removal
PWS (Password Stealer) Trojan Infection Removal