PKI Tutorials - Herong's Tutorial Examples - Version 2.04, by Dr. Herong Yang
Viewing Server Certificate Path in IE 10
This section provides a tutorial example on how to view certificate path when visiting a 'https' Web site in IE 10. The top certificate in a certificate path is the root CA certificate, which is trusted automatically.
When a browser validates a server certificate, it will try to build a certificate path - an ordered list of certificates that satisfy these conditions:
- The first certificate must a CA (Certificate Authority) certificate that is trusted by the browser.
- The subject of each certificate, except for the last, must be the issuer of the next certificate.
- The last certificate is the server certificate to be validated
Here is what I did to see the certificate path for https://login.yahoo.com Web site on IE 10.
1. Run IE 10 and go to https://login.yahoo.com and wait for the log in page to be loaded.
2. Click the lock icon at the end of the Web address field. A small pop up windows shows up.
3. Click the "View certificates" link on the pop up window. The Certificate dialog box shows up.
4. Click the "Certificate Path" tab. A certificate path with 3 certificates shows up:
VeriSign - The root CA certificate
|- VeriSign Class 3 Secure Server CA - G3
- The intermediate CA certificate
|- *.login.yahoo.com - The Web server certificate
5. Double click on "VeriSign" in the path. The root CA certificate dialog box shows up. The General tab shows that:
Issued to: VeriSign Class 3 Public Primary Certification Authority- G5 Issued by: VeriSign Class 3 Public Primary Certification Authority- G5 Valid from 11/7/2006 to 7/16/2036
6. Close the root CA certificate dialog box and double click on "VeriSign Class 3 Secure Server CA - G3" in the path. The intermediate CA certificate dialog box shows up. The General tab shows that:
Issued to: VeriSign Class 3 Secure Server CA - G3 Issued by: VeriSign Class 3 Public Primary Certification Authority- G5 Valid from 2/7/2010 to 2/7/2020
7. Close the intermediate CA certificate dialog box.
8. Now click the "General" tab on the original certificate dialog box:
Issued to: *.login.yahoo.com Issued by: VeriSign Class 3 Secure Server CA - G3 Valid from 4/7/2014 to 4/9/2015
What do you think about this certificate path? Should we trust login.yahoo.com now? I think this is a valid certificate path and we should trust login.yahoo.com, because:
- The root CA certificate "VeriSign Class 3 Public Primary Certification Authority - G5" is trusted because it was pre-installed in IE.
- The intermediate certificate "VeriSign Class 3 Secure Server CA - G3" is trusted because it was issued by a trusted root CA.
- The login.yahoo.com certificate "*.login.yahoo.com" is trusted because it was issued by a trusted intermediate CA.
The picture below shows you steps to reach the certificate path:
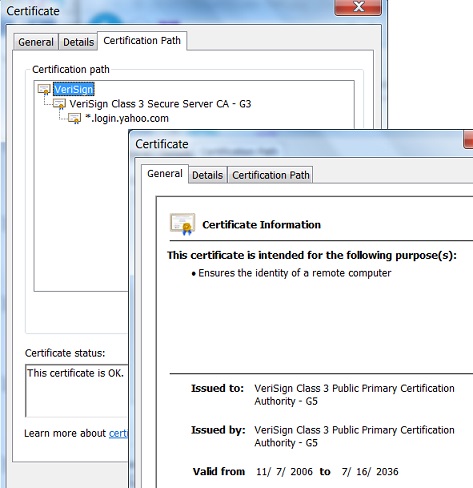
Table of Contents
Introduction of PKI (Public Key Infrastructure)
Introduction of HTTPS (Hypertext Transfer Protocol Secure)
►Using HTTPS with IE (Internet Explorer) 10
Visiting "https" Web Site with IE 10
Viewing Server Certificate Details in IE 10
►Viewing Server Certificate Path in IE 10
Installing Server Certificate Permanently in IE 10
Viewing Certificates in Certificate Stores in IE 10
Listing of Trusted Root CA in IE 10
Exporting Certificate to File from IE 10
Saving Server Certificate to File with IE 10
Deleting Certificates from IE 10
IE 10 Supporting Multiple Certificate Paths
IE 10 Reinstalling Root Certificates Automatically
Windows Automatic Root Update Mechanism
Perl Scripts Communicating with HTTPS Servers
PHP Scripts Communicating with HTTPS Servers
Java Programs Communicating with HTTPS Servers
Certificate Stores and Certificate Console
.NET Programs Communicating with HTTPS Servers
CAcert.org - Root CA Offering Free Certificates
PKI CA Administration - Issuing Certificates
Digital Signature - Microsoft Word 2007
Digital Signature - OpenOffice.org 3